If you think your go-to password is safe, think again. Despite countless warnings, many people still rely on common, easily guessable passwords for both personal and professional accounts. From predictable number strings to overused phrases, these weak choices continue to dominate the charts, making them prime targets for hackers. A recent report has revealed not one but two alarming lists—the 20 most popular passwords for personal use and another 20 for work accounts—credentials that could leave your data dangerously exposed. Before you type in your next login, find out if your password made either list—and why keeping it might be an open invitation to cybercriminals.
NordPass reveals the most dangerous passwords for work and personal accounts
While some passwords are notoriously bad across the globe, a new report from NordPass—a password manager created by the team behind NordVPN—shows there are clear differences in how people use them. The report reveals two troubling lists in the United States: the 20 weakest passwords for personal accounts and another 20 for work accounts. Both highlight just how risky Americans’ password habits remain.
To better understand the problem, NordPass analyzed millions of leaked credentials to identify the most common weak passwords in the U.S. The results are split into two categories: personal accounts, where people often prioritize convenience over safety, and work accounts, where weak choices can jeopardize entire organizations.
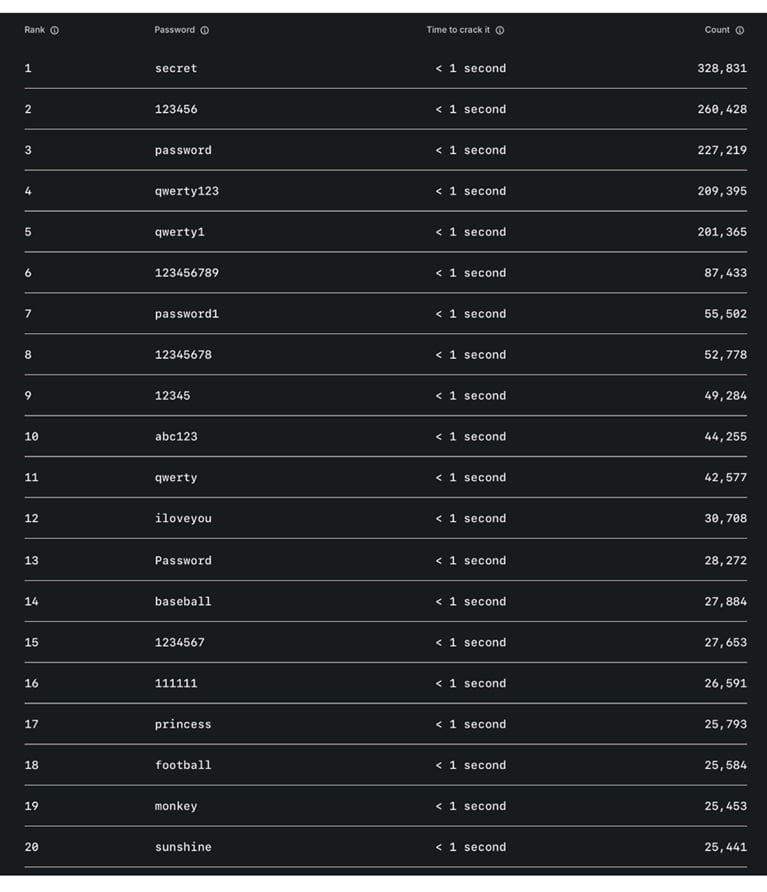
The 20 worst passwords for personal accounts in the U.S.
On the personal side, the most common offender is “secret”, used by more than 328,000 people and crackable in less than a second. Predictable number strings such as “123456” (260,428 uses) and “123456789” (87,433 uses) dominate the list, alongside classics like “password,” “qwerty,” and “abc123.” Even sentimental or simple words like “iloveyou,” “princess,” “monkey,” and “sunshine” appear, proving that emotional attachment doesn’t equal security. Every single password in this list can be broken almost instantly by hackers, leaving personal data wide open to attacks. See the complete list below:
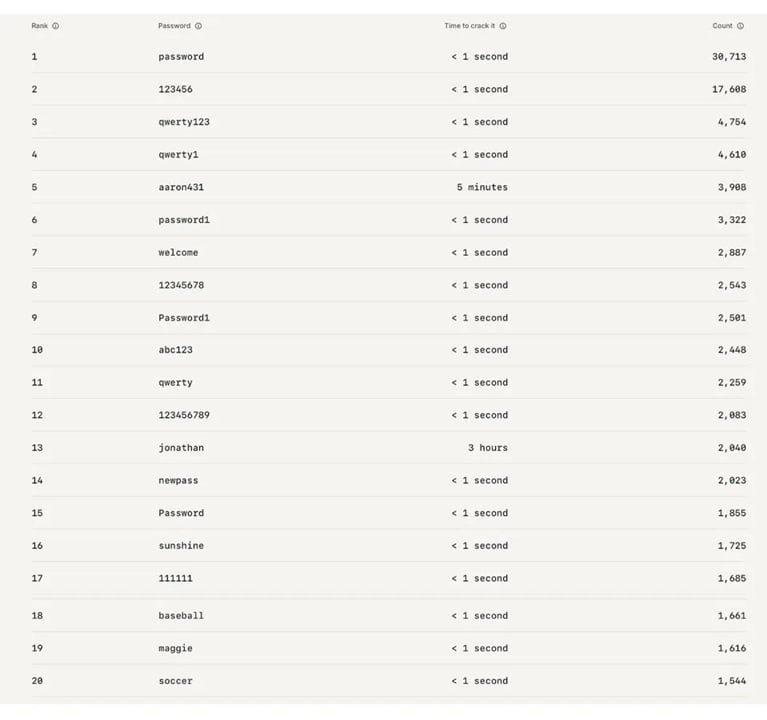
The 20 worst passwords for work accounts in the U.S.
When it comes to workplace security, the situation isn’t much better. At the top of the list is “password,” used over 30,000 times, followed by “123456” and “qwerty123.” Surprisingly, unique names like “aaron431” and “jonathan” show up, though they still offer little protection—hackers can guess them within minutes or hours. Other weak choices include “welcome,” “newpass,” “sunshine,” and “soccer.” Despite the professional setting, nearly every password on this list takes less than a second to crack, highlighting how employee carelessness can put entire organizations at risk. Check out the entire list below:
The risk of using weak passwords
Using simple or predictable passwords comes with major consequences. On personal accounts such as Google, Meta/Facebook, or Amazon, the danger is especially high when two-factor authentication (2FA) isn’t required—or when users rely on SMS-based one-time codes, which hackers can intercept or bypass with relative ease.
The stakes are even higher in the workplace. A single weak password can become the gateway to sensitive enterprise systems and networks, providing cybercriminals with an opening that could escalate into a full-scale ransomware attack against the entire organization.
To counter this, many companies now enforce 2FA on critical systems, a measure that blocks more than 99% of intrusion attempts. However, recent ransomware incidents highlight a worrying trend: instead of relying solely on technical hacks, attackers increasingly use social engineering tactics to trick employees into surrendering their 2FA codes.
Still, not every system is protected. All it takes is one overlooked account without strong safeguards, and attackers gain the foothold they need.
What you need to do
If any of your passwords are on either list, it’s important to act right away. Weak or reused credentials are a hacker’s easiest entry point. Here’s how you can protect yourself:
- Change your weak or repeated passwords immediately: Don’t just update the most important ones; make sure every account tied to a bad password is changed. Cybercriminals often try the same stolen password across multiple sites, which means a single compromised login could put your entire digital life at risk.
- Replace them with strong, unique passwords: A strong password should be long, unpredictable, and contain a mix of characters. Uniqueness is just as important; using the same password across different platforms means if one site is breached, all of your accounts are vulnerable.
- Rely on a dedicated password manager: While browser-based managers like Google’s built-in Chrome option are convenient, standalone password managers offer stronger encryption, better security features, and the ability to generate truly random credentials. These tools also make it easy to keep track of dozens (or even hundreds) of logins without cutting corners.
- Enable two-factor authentication: Adding a second step to your login process significantly reduces your risk, even if someone manages to get your password. Authenticator apps are safer than text message codes, which can be intercepted.
- Adopt passkeys wherever possible: Passkeys, which use cryptographic authentication instead of typed passwords, are quickly becoming the gold standard for online security. They’re resistant to phishing, nearly impossible to brute-force, and supported by more and more platforms each year.
Source: Forbes

